Environment
The C360 solution is deployed on a modern, scalable, and cloud-native architecture that leverages both AWS and Snowflake to enable secure, efficient, and future-proof data operations.
Overview
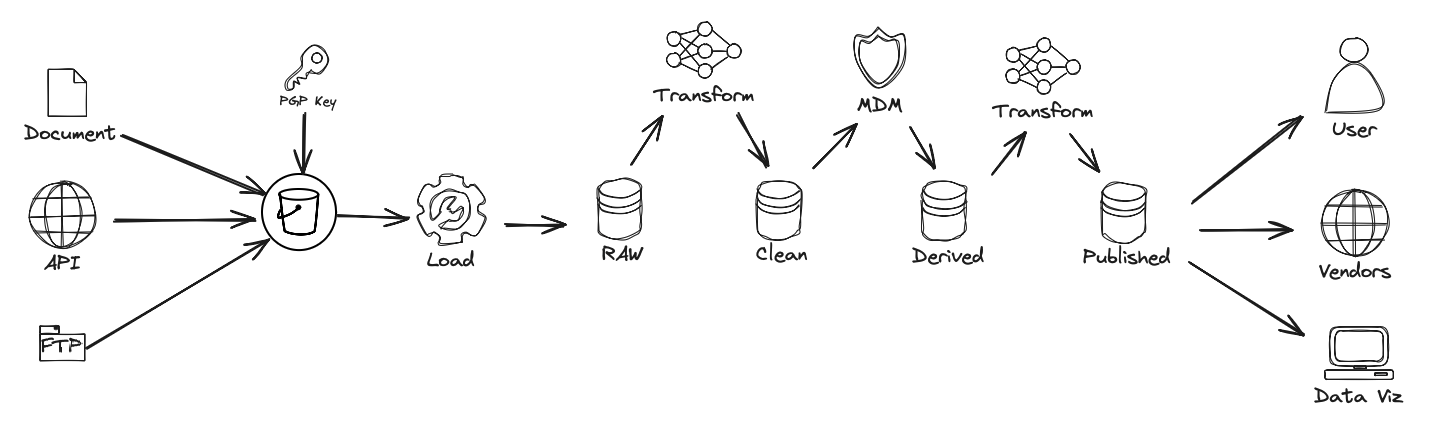
The environment follows a hybrid cloud architecture: - AWS is used for ingestion, processing, orchestration, and file storage. - Snowflake serves as the core data warehouse and analytical platform, following a medallion architecture pattern.
☁️ Cloud Infrastructure: AWS
Amazon Web Services (AWS) powers the data pipeline orchestration and transformation layer. Key AWS services include:
| Service | # Instances | Role in the C360 Ecosystem |
|---|---|---|
| S3 | 800 | Secure storage for raw data files, staging zones, and external ingestion. |
| Lambda | 1600 | Event-driven compute for lightweight ETL tasks, file processing, and triggers. |
| Glue | 4 | Managed ETL service used for cataloging, schema detection, and heavy transformations. |
🔁 Data Ingestion Pipeline
- Source systems drop data files or events.
- AWS Lambda functions detect and trigger workflows.
- AWS Glue jobs clean, structure, and enrich the incoming data.
- Transformed data is loaded into Snowflake for storage and analytics.
🧊 Data Warehouse: Snowflake
Snowflake is the central platform for storage, query processing, and data sharing. It implements a medallion architecture, ensuring data traceability and quality control across the lifecycle.
🏅 Medallion Architecture Stages
| Layer | Description |
|---|---|
| Raw | Unmodified data as ingested from source systems. |
| Clean | Data after initial parsing, validation, and deduplication. |
| Derived | Transformed and enriched datasets ready for business consumption. |
| Published | Final curated tables and views exposed to downstream consumers and apps. |
🔍 Observability & Governance
- Role-based access control and row-level security are implemented in Snowflake to protect sensitive data.
- Data quality checks are applied at each medallion stage.
- Time travel and cloning are leveraged for non-destructive debugging and backtesting.
🔧 Integration and Monitoring Tools
| Tool / Layer | Description |
|---|---|
| Custome Made Solution | For monitoring data streams and operations. |
| CloudWatch / SNS | For alerts and operational monitoring (AWS-native). |
| Dynatrace | For internal scheduling and change tracking. |
📐 Design Principles
- Modular & Serverless: Event-driven, decoupled services for flexibility and cost efficiency.
- Secure by Design: Encryption at rest and in transit, with fine-grained access policies.
- Scalable & Resilient: Cloud-native architecture supporting batch and (optionally) streaming workloads.
- Auditable: Logs and metadata are retained and queryable for auditing and traceability.
🔄 Data Flow Diagram
The following diagram illustrates the high-level data flow across AWS and Snowflake in the C360 platform:
flowchart TD
subgraph Source Systems
A1(Dealer Systems)
A2(Internal Systems)
A3(External Vendors)
end
subgraph AWS Layer
B1(S3 - Raw File Landing)
B2(Lambda - Trigger ETL)
B3(Glue Jobs - Transform & Catalog)
end
subgraph Snowflake
C1(Raw Layer)
C2(Clean Layer)
C3(Derived Layer)
C4(Published Views)
end
subgraph Consumers
D1(Business Analysts)
D2(Digital Products)
D3(Dashboards & Reports)
end
A1 --> B1
A2 --> B1
A3 --> B1
B1 --> B2 --> B3 --> C1
C1 --> C2 --> C3 --> C4
C4 --> D1
C4 --> D2
C4 --> D3Security & Access Management
Security is foundational to the C360 architecture. The platform employs a multi-layered security model encompassing role-based access controls, data encryption, and comprehensive audit logging. This ensures that sensitive customer data remains protected while authorized users can securely access the information they need, when they need it.
🧑💼 Identity & Access Control
AWS
| Control Layer | Implementation |
|---|---|
| IAM Roles & Policies | Applied to Lambda, Glue, and S3 to restrict service-level access. |
| S3 Bucket Policies | Fine-grained permissions based on roles and data zones. |
| KMS Encryption | Used for encrypting data at rest (S3, Glue metadata). |
Snowflake
| Access Layer | Implementation |
|---|---|
| Role-Based Access | Hierarchical roles (e.g., VIEWER, ANALYST, ENGINEER, ADMIN) |
| Row-Level Security | Dynamic filters based on user role, region, or assigned customer groups |
| Object-Level Grants | Access to databases, schemas, and tables controlled through custom roles |
| Time Travel Controls | Allows auditing or recovery of historical data versions without unauthorized exposure |
🔐 Data Protection
| Protection Type | Technique |
|---|---|
| At Rest | Encryption via AWS KMS (S3, Glue) and Snowflake native encryption |
| In Transit | TLS encryption for all inter-service and client connections |
| PII Handling | Masking and tokenization supported where applicable in the Published layer |
| Audit Logs | Tracked in Snowflake (via QUERY_HISTORY, ACCESS_HISTORY) and AWS CloudTrail |
🧪 Monitoring & Alerting
| Tool / Layer | Purpose |
|---|---|
| AWS CloudWatch + SNS | Alerts for Lambda, Glue, and pipeline failures |
| Snowflake Access Logs | Monitoring of suspicious queries or permission misuse |
| Scheduled Review | Regular access review cycles and privilege audits |
✅ Governance Integration
The Data Office maintains stewardship over: - Role definitions and user onboarding workflows - Approval matrix for access to sensitive datasets - Periodic compliance reviews in coordination with IT security
This security framework ensures that C360 complies with enterprise policies and regulatory expectations, while maintaining agility and usability for data-driven innovation.
This environment is designed to be maintainable, transparent, and evolvable—supporting the long-term goals of the C360 initiative while enabling new data products and business capabilities.